ESAA&ODM
Embedded Security Adaptation Approach (ESAA)
The design of embedded security complies with Embedded Security Adaption Approach (ESAA). The concept is built on trinity of vulnerability, threat and risk. Each of the aspects is closely scrutinized so as to tailor a cost-efficient solution for our customers.
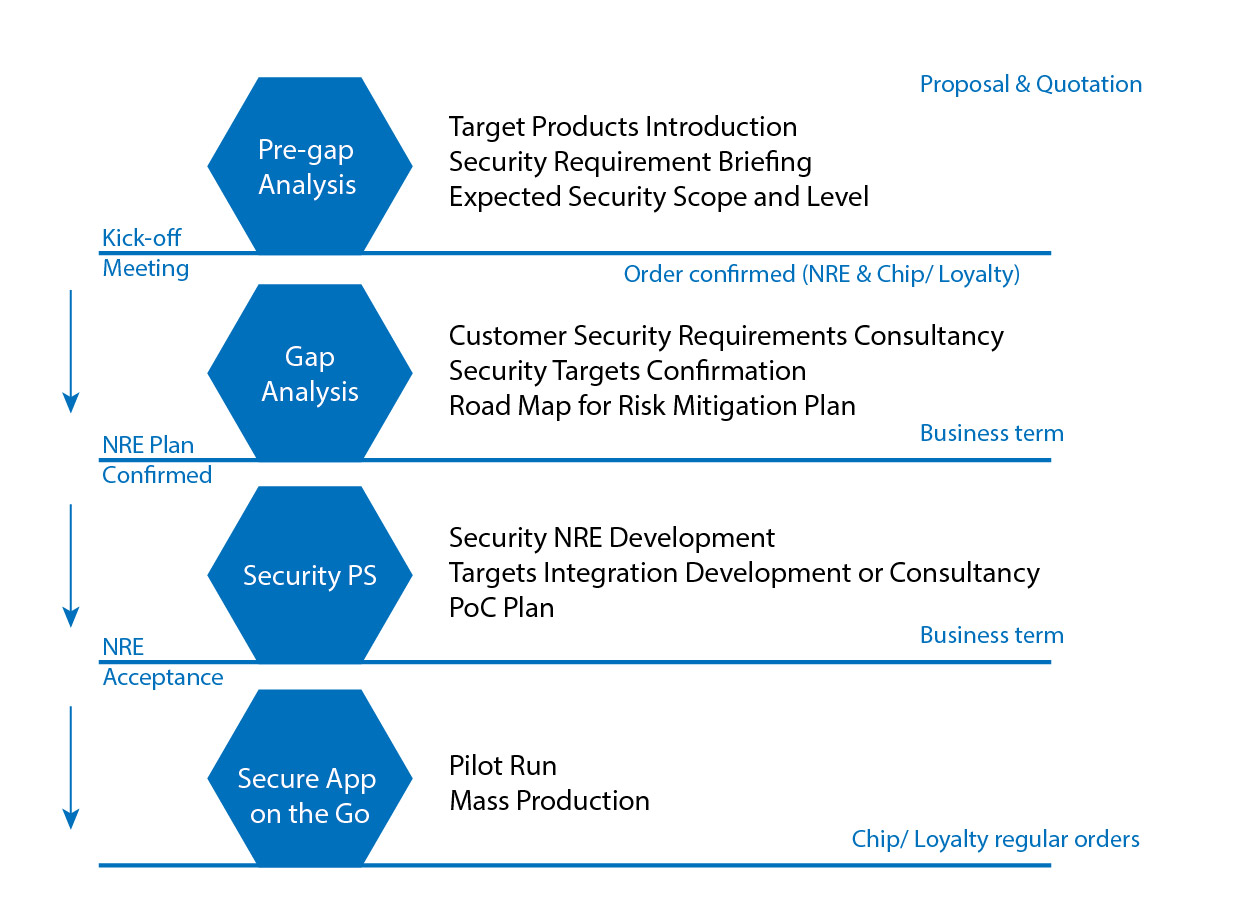
The phases of ESAA are as follows.
- Pre-gap analysis - introduction of target products, briefing of security requirement, and expected security scope and level
- Gap analysis - consultancy of security requirements, confirmation of security objectives, and road map for risk mitigation
- Security PS - security NRE development, target integration and consultancy, and PoC plan
- Secured App on the go - pilot run and mass production
Original Design Manufacturer (ODM)
We provide ODM service of security mechanisms. From plan, design and implementation, their security-related products are instilled with robust IKV solutions inside. Here are our successful stories:
Cryptographic module for voice telecommunication machines
We help clients design cryptographic modules that carry out timely encryption for communication data of either frequency-hopping spread spectrum or constant bandwidth.
High-performance cryptographic module
We help our clients design the high-speed cryptographic module. The module fits SD/USB interfaces and encrypts information at a high speed.
FIDO2 Security Key ODM Service
Passwordless and multi-factor authentication is on the rise. Enterprises are seeking turnkey solutions to build their own FIDO2 USB Key. We provide FIDO USB ODM service for enterprises to make their own key.
Standard Procedure of ESAA
ESAA Architecture