Cryptocurrency
Hardware-base wallets for emerging digital assets
Over the past five years, an increase in the number of cryptocurrency hacks has raised the alarm about security breaches in transaction and deposit. The public started to dive into the mechanism and realized transaction is approved through cryptography.
As the underlying mechanism, cryptography and blockchain, became salient, awareness of private key was raised. The private key is bound to an account. It is used to sign a transaction block for the approval of asset transfer. If it is known by others, assets are likely to be stolen.
The cryptocurrency wallet platform aims to provide building blocks for customers who intend to design “cold wallet” to securely store private keys. We offer know-how in cryptographic algorithms, key generation, key establishment, key exchange; that is the entire life cycle of key management and cryptographic functions.
With IKV-Tech’s expertise, our customers has achieved mass production in only few years without any security breach exposed. The products we collaboratively designed won the 2020 CES Innovation Award and eventually become the global top players.
Over the past five years, an increase in the number of cryptocurrency hacks has raised the alarm about security breaches in transaction and deposit. The public started to dive into the mechanism and realized transaction is approved through cryptography.
As the underlying mechanism, cryptography and blockchain, became salient, awareness of private key was raised. The private key is bound to an account. It is used to sign a transaction block for the approval of asset transfer. If it is known by others, assets are likely to be stolen.
The cryptocurrency wallet platform aims to provide building blocks for customers who intend to design “cold wallet” to securely store private keys. We offer know-how in cryptographic algorithms, key generation, key establishment, key exchange; that is the entire life cycle of key management and cryptographic functions.
With IKV-Tech’s expertise, our customers has achieved mass production in only few years without any security breach exposed. The products we collaboratively designed won the 2020 CES Innovation Award and eventually become the global top players.
- Unique preloader dedicated to product/vendor
- Elliptic Curve Cryptography Curves (sec256k1, ed25519)
- Verification with hashing (SHA-2, SHA-3 family)
- BIP32, BIP39 (PBKDF2), BIP44 path (multiple currencies)
Key Features
- Unique preloader dedicated to product/vendor
- Elliptic Curve Cryptography Curves (sec256k1, ed25519)
- Verification with hashing (SHA-2, SHA-3 family)
- BIP32, BIP39 (PBKDF2), BIP44 path (multiple currencies)
For systems processing transaction, confidential data and digital content, IKV-Tech aims to construct a pertinent subsystem, which can grant possessors complete control over the digital assets in transit and at rest.
Typically, users store keys in their computers to transact. Under the circumstance, hackers’ trick can be
- spreading modified wallet software so as to transfer users’ coins to their accounts
- using malware and appropriating users’ keys, wallet files and passwords.
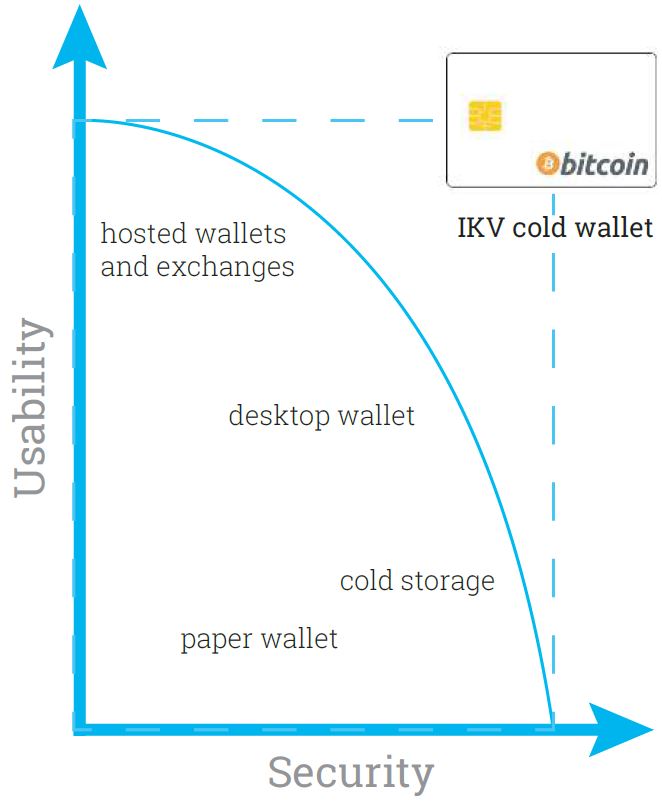
To address the issues mentioned above, storing keys in a secure hardware device is the trend of designing cryptocurrency wallets. The wallet is activated on a need-basis only, ensuring most of the time it is offline and will not be connected to public network. Since the wallet isolates private keys from “hot” connected environments, it is called "cold wallet".
Leverage IKV-Tech Expertise
For systems processing transaction, confidential data and digital content, IKV-Tech aims to construct a pertinent subsystem, which can grant possessors complete control over the digital assets in transit and at rest.
Typically, users store keys in their computers to transact. Under the circumstance, hackers’ trick can be
- spreading modified wallet software so as to transfer users’ coins to their accounts
- using malware and appropriating users’ keys, wallet files and passwords.
To address the issues mentioned above, storing keys in a secure hardware device is the trend of designing cryptocurrency wallets. The wallet is activated on a need-basis only, ensuring most of the time it is offline and will not be connected to public network. Since the wallet isolates private keys from “hot” connected environments, it is called "cold wallet".
Bitcoin Secure Element
We have launched a Bitcoin wallet called BCSE (Bitcoin Secure Element) based on our extensive experiences with chip firmware and cryptographic algorithms. The BCSE uses a cryptography chip to perform Bitcoin's signature algorithm (ECDSA) and functions as a virtual wallet. This chip can be embedded into smart cards or any devices.
This chip has passed Common Criteria EAL 5+ international security certification, ensuring security of storage space. It also provides multiple secure authentication mechanisms and allows users to set their favorable security level. The APDU command specification and host libraries are open to the public for wallet software integration. Currently, customized Bitcoin-Core and Multibit are available for BCSE users and wallet developers.
Platform for Customized Wallets
Bitcoin Secure Element
We have launched a Bitcoin wallet called BCSE (Bitcoin Secure Element) based on our extensive experiences with chip firmware and cryptographic algorithms. The BCSE uses a cryptography chip to perform Bitcoin's signature algorithm (ECDSA) and functions as a virtual wallet. This chip can be embedded into smart cards or any devices.
This chip has passed Common Criteria EAL 5+ international security certification, ensuring security of storage space. It also provides multiple secure authentication mechanisms and allows users to set their favorable security level. The APDU command specification and host libraries are open to the public for wallet software integration. Currently, customized Bitcoin-Core and Multibit are available for BCSE users and wallet developers.


Success Stories about Our Customers




