SW Protection
The digitization of enterprise data has become the mainstream in the IT field. All the information such as enterprises’ financial data, clients’ information, research results, invaluable knowledge bases can be easily searched, modified, transmitted, and stored. However, what follows are those intruders, information leaks, unwarranted modification or even deletion. One way or another, threats put enterprises into jeopardy.
Fortunately, there is Application & Content Protection (ACP). This security solution aims to help those in need but without astronomical sums of capitals to enhance IT security in the face of adverse impacts of risks and deteriorating IT environments. It applies to IT systems like ERP (Enterprise Resource Planning) and CRM (Customer Relationship Management) and knowledge products like electronic galleries, e-books, digital textbooks and so on.
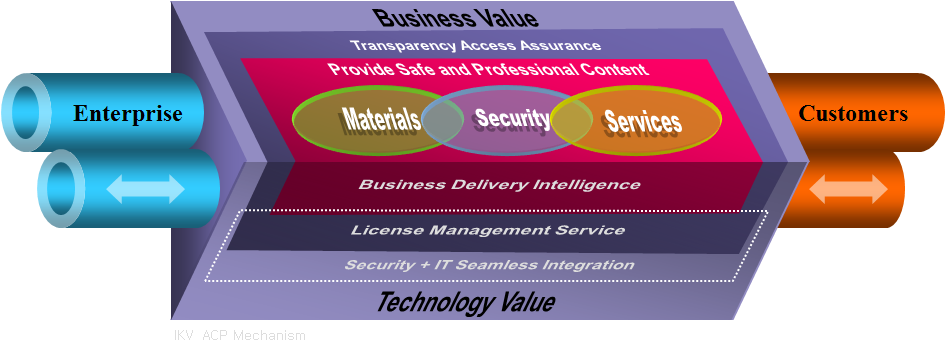
The picture illustrates seamless integration of ACP with business value and technical value. Following implementation of ACP, precious contents are available for clients and equipped with robust ACP encryption and strong authentication.
ACP Wizard dramatically upgrades the security of original systems in a few simple steps, preventing threats from copying, appropriating and even skimming. In addition, the patent transparent real-time encryption engine exceptionally encrypts data within the operating system, leaving threats that exploit apps’ vulnerabilities ignorant of multilayer protection ACP has executed onto the OS.
Multiple Identity Authentication Modes
(Evaluated according to budgets and requirements)
- Software mode: lowest cost, invalid and failed copy attempt.
- Smart card mode: high cost, card readers required, robust authentication mechanism in the IT field
- USB Key mode:moderate cost, less secure than the Smart card mode.
Hardware Environment Forensic Technique
This technique wards off illegal copy since ACP is able to identify features of hardware environment and generates encryption keys based on hardware environment. Any attempt to copy will fail even with an ISO virtual drive.
ACP Product
ACP for windows
VDP, Virtual Drive Protection
VDP-R, VDP Recordable
ACP for Linux
LED, Linux Encryption Drive
Linux applications and content protection in OEM model
ACP Specification
- Loadable windows driver module (Linux v2.6, WinXP, 2003, Vista, XPE,Win7)
- Running above physical Ext2/Ext3/NTFS file-system partition
- Real-time encryption of raw sectors
- Support token as key storage
- Locked by host or by key token
- Cryptographic algorithms: T-DES/DES, AES, RC5, and Cast
- Provide application authorization
- Protect application from memory dump cracking
- Cipher shell tool to protect application run-time memory
- License management
The digitization of enterprise data has become the mainstream in the IT field. All the information such as enterprises’ financial data, clients’ information, research results, invaluable knowledge bases can be easily searched, modified, transmitted, and stored. However, what follows are those intruders, information leaks, unwarranted modification or even deletion. One way or another, threats put enterprises into jeopardy.
Fortunately, there is Application & Content Protection (ACP). This security solution aims to help those in need but without astronomical sums of capitals to enhance IT security in the face of adverse impacts of risks and deteriorating IT environments. It applies to IT systems like ERP (Enterprise Resource Planning) and CRM (Customer Relationship Management) and knowledge products like electronic galleries, e-books, digital textbooks and so on.
The picture illustrates seamless integration of ACP with business value and technical value. Following implementation of ACP, precious contents are available for clients and equipped with robust ACP encryption and strong authentication.

ACP Wizard dramatically upgrades the security of original systems in a few simple steps, preventing threats from copying, appropriating and even skimming. In addition, the patent transparent real-time encryption engine exceptionally encrypts data within the operating system, leaving threats that exploit apps’ vulnerabilities ignorant of multilayer protection ACP has executed onto the OS.
- Software mode: lowest cost, invalid and failed copy attempt.
- Smart card mode: high cost, card readers required, robust authentication mechanism in the IT field
- USB Key mode:moderate cost, less secure than the Smart card mode.
ACP for windows
VDP, Virtual Drive ProtectionVDP-R, VDP Recordable
ACP for Linux
LED, Linux Encryption DriveLinux applications and content protection in OEM model
- Loadable windows driver module (Linux v2.6, WinXP, 2003, Vista, XPE,Win7)
- Running above physical Ext2/Ext3/NTFS file-system partition
- Real-time encryption of raw sectors
- Support token as key storage
- Locked by host or by key token
- Cryptographic algorithms: T-DES/DES, AES, RC5, and Cast
- Provide application authorization
- Protect application from memory dump cracking
- Cipher shell tool to protect application run-time memory
- License management



