Market
Security facilitates corporate image-building
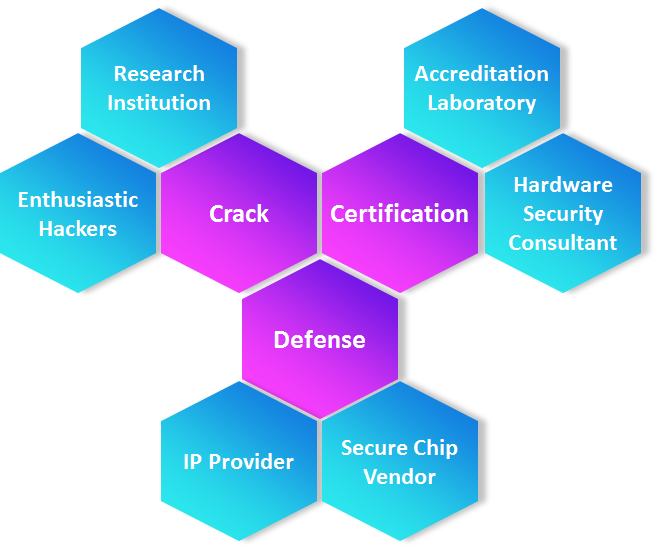
There are mainly two types of clients searching for security solutions: successful businessmen who become the target of hackers because of increasing popularity and profit gain, and high-end OEMs who have urgent requirements for security. As security becomes a must rather than an option, they reached IKV-Tech for professional security solutions.
Once our clients realize how security facilitates corporate image-building and meets OEM requirements, they are galvanized into action aimed at risk assessment and even become our partners.
Embedded hardware ecosystem architecture
As IKV-Tech perfectly understands the architecture of embedded device ecosystems, we help clients make clear of their need for security and provide professional security solutions.
The embedded hardware ecosystem architecture is as follows.
There are mainly two types of clients searching for security solutions: successful businessmen who become the target of hackers because of increasing popularity and profit gain, and high-end OEMs who have urgent requirements for security. As security becomes a must rather than an option, they reached IKV-Tech for professional security solutions.
Once our clients realize how security facilitates corporate image-building and meets OEM requirements, they are galvanized into action aimed at risk assessment and even become our partners.
As IKV-Tech perfectly understands the architecture of embedded device ecosystems, we help clients make clear of their need for security and provide professional security solutions.
The embedded hardware ecosystem architecture is as follows.

Our clients are companies from all fields of the electronics industry as well as governmental and business entities
- Taiwan best-selling gaming machine brands
- Digital content providers
- Mobile phone and encrypted communication software
- CNC equipment
- Automation & control gear design
- Military communication systems
- Cryptocurrency and blockchain service provider
- OS protection
- standard security chips
- customized hardware security
- MCU protection
Our platforms include cryptographic algorithm IPs, security chips, IoT device identification, key management and secure administration mechanisms, cryptocurrency wallets and hardware security modules (HSM).
- Cryptographic chips: security chip, secure element, silicon IP
- Hardware-based security modules: USB authentication tokens, USB OTP (One Time Password) tokens, ISO-7816/SIM-sized OTP generators, FAT/FAT32 encryption modules, dynamic password authentication (HOTP) module, PCIe high-speed security module, MicroSD encryption card, Fusion USB security module
- Software protection: Windows & Linux access control
- Firmware protection: Secure Update Service (SUS)
- Bitcoin wallet: BCSE (Bitcoin Secure Element)
- Hardware-based security programs for the Internet of Things (IoT)
Our clients
Our clients are companies from all fields of the electronics industry as well as governmental and non-governmental organizations
- Taiwan bestselling gaming machine brands
- Digital content providers
- Mobile phone and encrypted communication software
- CNC equipment
- Automation & control gear design
- Military communication systems
- Cryptocurrency and blockchain service provider
Service and platform
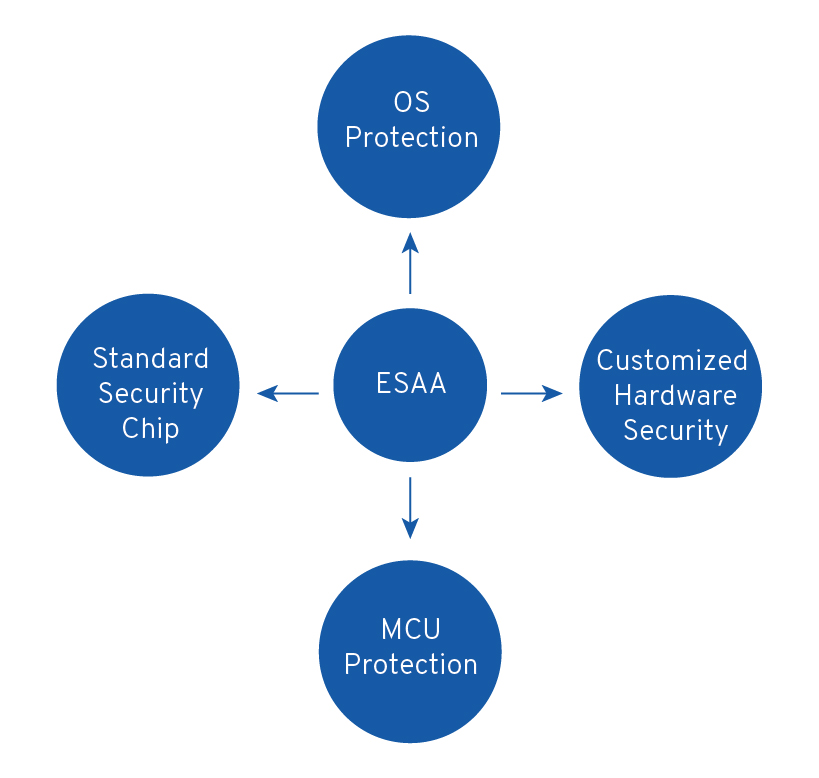
Based on ESAA (Embedded Security Adaption Approach), we specialize in
- OS protection
- standard security chips
- customized hardware security
- MCU protection

Our platforms include cryptographic algorithm IPs, security chips, IoT device identity, key management and secure administration mechanisms, cryptocurrency wallets and hardware security modules (HSM).
- Cryptographic chips: security chip, secure element, silicon IP
- Hardware-based security modules: USB authentication tokens, USB OTP (One Time Password) tokens, ISO-7816/SIM-sized OTP generators, FAT/FAT32 encryption modules, dynamic password authentication (HOTP) module, PCIe high-speed security module, MicroSD encryption card, Fusion USB security module
- Software protection: Windows & Linux access control
- Firmware protection: Secure Update Service (SUS)
- Bitcoin wallet: BCSE (Bitcoin Secure Element)
- Hardware-based security programs for the Internet of Things (IoT)



