Expertise
Cryptographic algorithms
- Implementation
- Security analysis
- Key establishment
- PKC (Public Key Cryptography) operations
Chip protection
- Real security threats and mitigation tactics
- Side-channel attack
Embedded system security standards
- Security analysis of production procedures
- Device identity management
- Device life cycle management
Mass-production security
- Design-stage security analysis
- Security policy planning
- Key management
Micro-controller security
- Crypto algorithm libraries
- Basic security libraries
- Security protocol design and implementation
- Embedded firmware and driver design
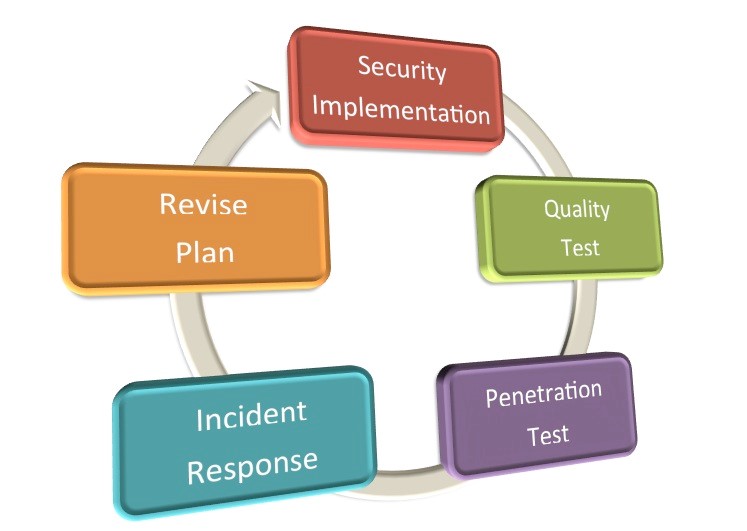
PDCA (Plan, Do, Check, Act)
To build a robust and secure system, a strict reviewing process is crucial. We thus follow the ISO-9001 PDCA (Plan, Do, Check, Act) principle to guarantee high-quality services. Adjusted to the field of security engineering, the PDCA cycle encompasses the following elements
- Implementation
- Quality testing
- Penetration testing
- Incident response
- Revision
Key to heightened security
Based on software engineering building blocks, we particularly focus on
- Penetration Test
- Incident Response
In the first one, we examine the potential loophole in implementation from hackers’ point of view in order to monitor the security of clients’ products even after transaction.
In the second one, we keep track of changes in the security industry, updating our strategies against algorithmic flaws, OS weakness and potential threats, executing timely response to incidents.
- Implementation
- Security analysis
- Key establishment
- PKC (Public Key Cryptography) operations
- Real security threats and mitigation tactics
- Side-channel attack
- Security analysis of production procedures
- Device identity management
- Device life cycle management
- Design-stage security analysis
- Security policy planning
- Key management
- Crypto algorithm libraries
- Basic security libraries
- Security protocol design and implementation
- Embedded firmware and driver design
To build a robust and secure system, a strict reviewing process is crucial. We thus follow the ISO-9001 PDCA (Plan, Do, Check, Act) principle to guarantee high-quality services. Adjusted to the field of security engineering, the PDCA cycle encompasses the following elements
- Implementation
- Quality testing
- Penetration testing
- Incident response
- Revision

- Penetration Test
- Incident Response
In the first one, we examine the potential loophole in implementation from hackers’ point of view in order to monitor the security of clients’ products even after transaction.
In the second one, we keep track of changes in the security industry, updating our strategies against algorithmic flaws, OS weakness and potential threats, executing timely response to incidents.



